In today’s world, Security is the most worrying factor. Cybercrime is the biggest threat to any online business in the world, and ecommerce sites are the most lucrative target as they contain confidential, personal and payment information as necessary to complete a transaction. Furthermore, unauthorized persons may also take advantage of vulnerabilities to redirect clients to domains owned by malicious / attackers, and may manipulate, alter the order details. As a result, a compromised site can endanger its consumer identity and financial loss to business as well as loss of user confidence and unwanted litigation threats. Therefore, this document outlines Bagisto Security Standards required to maintain a secure environment and how all security controls, procedures, and protections should be implemented to protect yourself from any type of attack by creating awareness within you.

General Server and User End Security Standards to make your bagisto store less attractive target and to make it more secure than ever :
Run your entire store over HTTPS (Google now uses HTTPS as a ranking factor)
However, HTTPS avoids eavesdropping attacks, and ensures secure communication between the users and websites.
Protect your infrastructure including your server, web applications, users, and network connection
- Keep all of the services and softwares up to date on the server and also install the newly discovered security patches quickly.
- Bagisto
- database
- adminer/phpmyadmin
- apache
- redis, etc
- Similarly, always ensure that the server operating system is up to date and is running in a secure environment.
- Manage files with only secure protocols of communication (SSH / SFTP / HTTPs), disable FTP.
- Disable unused ports, and stop services running unnecessarily.
- Use of [.htaccess] file, when using apache web server to protect system files.
- Restrict access to certain IPs to the admin panel and use Admin logins with two-factor authorization.
- Use of strong and unique passwords.
- Use a properly configured and updated firewall between the payment card data and the public network.
Restrict files with .git .zip .gz .sql extension
- Edit your .htaccess file.
|
1 2 3 |
<FilesMatch "\.(git|zip|tar|sql)\$"> Require all denied </FilesMatch> |
- Besides this, review your server for development leftovers and also make sure that there are no accessible “log files”, “.git directories”, “database dumps”, “zip files”.
Restrict php execution inside storage directory
- Moreover, Edit your apache configuration file.
|
1 2 3 4 5 6 |
<Directory "~/www/bagisto/public/storage/"> <FilesMatch "\.php\$"> Require all denied </FilesMatch> php_flag engine off </Directory> |
Limiting error messages
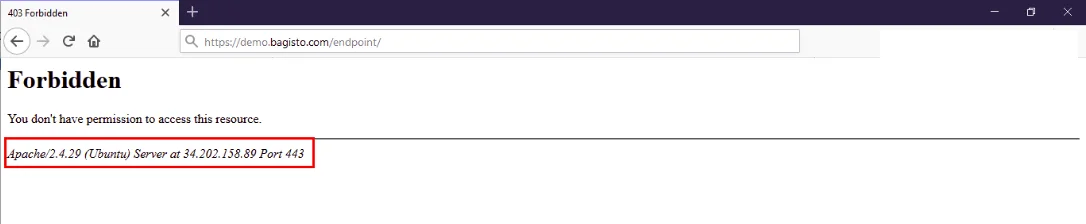
- Edit your apache configuration file to avoid displaying server and os details.
- Set “ServerSignature” to OFF as by default it is ON.
- Add “ServerTokens Prod” to display Apache as product only.
Harden your server
- Use of mod_security module to detect and prevent intrusions.
- Use of mod_passive module to prevent brute force attack.
- Allow only specific users to login.
- Disable login to users with empty password.
- Check iptable rules to prevent unauthorized access and activity.
- Take regular backup of important files and also save them remotely in a secure environment.
Implementaion of HTTP security headers
In addition, Headers play a key role in communication between the client and the server, some of them have been mentioned in order to enhance the web security.
- HTTP Strict Transport Security (HSTS).
- Content Security Policy (CSP).
- Cross Site Scripting Protection(X-XSS-Protection).
- X-Frame-Options.
- X-Content-Type-Options.
Continuous logging and monitoring
- Likewise, Monitor all access to the network and cardholder data environment.
- Keep eye on Large volume orders for a single item from a new customer.
- A series of orders, shipped to the same address using different payment methods.
Conclusion
As every day passes, Security is becoming increasingly critical, but if it is not applied correctly, Security can also end up becoming a double-edged sword. Hence, the purpose of this Guide is to provide you with best Security Standards for the consumer’s equation side. Thus, we suggest you to take some time out of your day to enjoy our blog and to learn about the ways we’ve mentioned.
In case of any help, query, or feedback please contact us or raise a ticket.
Thank you for reading this article,
Keep in touch!!



Be the first to comment.